Last week I gave a high level overview of the AWS Control Tower solution - one of AWS’s approaches to ease the transition to the cloud. It helps answer the question - how do I start? - and allows customers to on-board with standardisation and best practice baked in. But why is it needed in the first place?
Most people learn about the cloud in its components and when it comes to putting it together into a connected way they are left staring into space not really knowing the best way to piece it all together. Since every organisation's integration challenges will be unique, in some ways it is hard to come up with a one size fits all solution.
The term “Landing zone” is a common term used across all cloud providers to define the starting point from which your organisation can quickly launch and deploy workloads and applications with confidence. Each provider takes a different approach so it is worthwhile to take a quick look and compare how each provider helps customers get started building their landing zone.
First, let’s review what the key components of what a landing zone should contain:
Organisational Setup
Identity and access management
Networking
Initial security baseline
Guardrails/Policies
Billing and management
Logging and monitoring
Governance
AWS
AWS recommends using a multi-account framework strategy as a single account provides the highest level of resource isolation and security. It is recommended you use different accounts for different business units, projects, dev teams, dev, test, prod etc. AWS’s main way to support multi-accounts is through a managed service called AWS Organisations. AWS Organisations helps set up new accounts into a hierarchy, set security policies and customise your environments to best fit your business needs.
AWS has three key options to help create your landing zone:
Managed service based landing zone using AWS Control Tower ,
CloudFormation solution built using AWS Landing Zone, and
Customised landing zone that you build.
Each option requires a different level of AWS knowledge.
AWS Control Tower
AWS Control Tower is AWS’s preferred solution. If you haven’t set up a landing zone yet, it is the easiest and safest way to get started. It is a UI based approach and you can literally get a baseline setup in a couple of hours.
AWS Control Tower runs as an AWS managed service. When you’re looking for a pre-packaged environment solution out of the box, you can use AWS Control Tower for prescriptive guidance and a fully managed environment. The service sets up a landing zone based on multi-account best practices, centralises identity and access management, and establishes pre-configured governance rules for security and compliance.
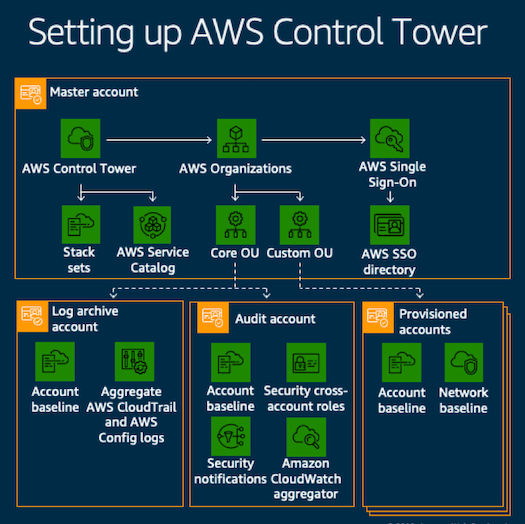
In more detail, some of the blueprints implemented on AWS Control Tower include:
A multi-account environment using AWS Organizations
Identity management using AWS Single Sign-On (AWS SSO) default directory
Centralised logging from AWS CloudTrail, and AWS Config stored in Amazon Simple Storage Service (Amazon S3)
Cross-account security audits using AWS Identity and Access Management (IAM) and AWS SSO
A set of guardrails that provide ongoing governance for your overall AWS environment.
It also provides:
Ability to automate your account provisioning workflow with an account factory
A dashboard to provide visibility into your organisational units, accounts and guardrails
Even though AWS Control Tower is a great way to setup the baseline implementation, your team will still need a good amount of knowledge to understand what is doing as it requires some tailoringto finish it off.
Landing Zone Solution
Similar to the AWS Control tower solution, the Landing Zone Solution helps customers quickly set up a secure, multi-account AWS environment base using AWS best practices. However instead of using an UI, it comes as a set of cloud formation scripts that can be configured as required. Hence, it is also likely to take more time to test and deploy as well.
The end result is a setup using the same best practices as the AWS Control Tower solution but provides a lot more flexibility with its customisations. Of course the caveat is that it requires more AWS expertise to setup and maintain.
The following are the core components it helps create based on a set of parameters.
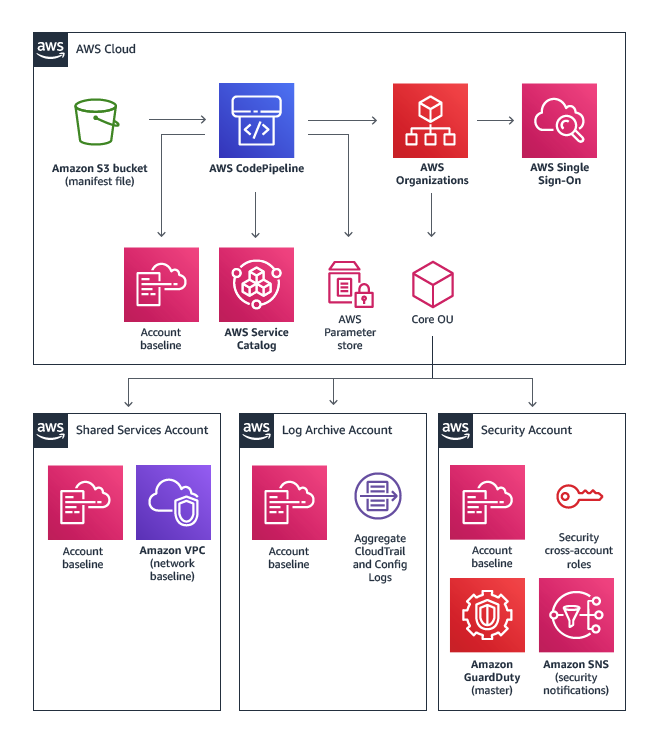
Custom-built landing zone
You can also choose to build your own customised landing zone solution. In this case, you have to implement the baseline environment to get started with identity and access management, governance, data security, network design, and logging. AWS recommends this approach if you want to build all of your environment components from scratch, or if you have requirements that only a custom solution can support. You must have enough expertise in AWS to manage, upgrade, maintain, and operate the solution once it’s deployed.
References
Setting up a secure and scalable multi-account AWS environment - AWS Prescriptive Guidance
Azure
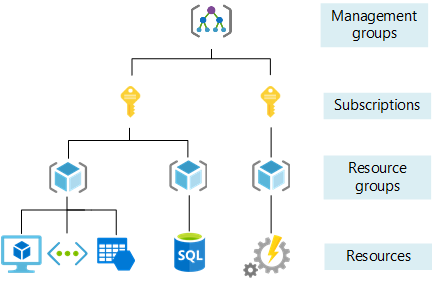
Azure uses a combination of subscriptions and resource groups to manage its resource isolation. Billing is typically at a subscription level while policy enforcement and compliance is done at the management group level.
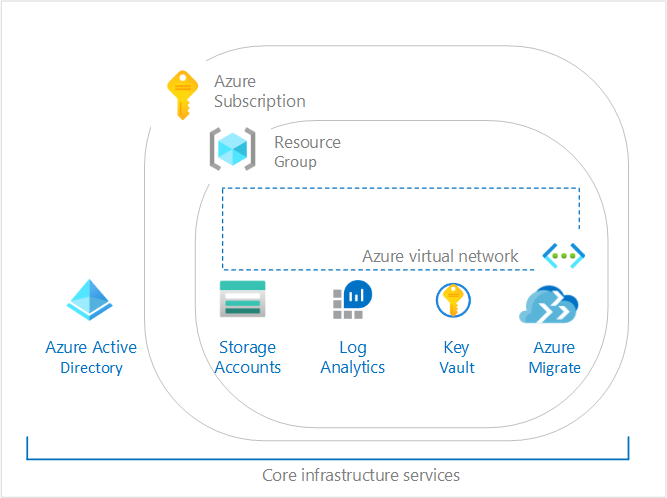
Azure also has the concept of a landing zone solution although it more heavily relies on a combination of documentation and blueprints to set up their landing zone and then a refactoring mindset as requirements evolve.
Azure Blueprints enables an organisation to define a repeatable set of Azure resources that implements and adheres to an organisation’s standards, patterns, and requirements. Azure Blueprints makes it possible for development teams to utilise pre-built components (eg networking) for rapid build and stand up of new environments with confidencethey’re building within organisational compliant framework. This speeds up development and delivery.
Below, I have highlighted some of the key blueprints.
Migration Landing Zone Blueprint
The Cloud Adoption Framework (CAF) Migration landing zone blueprint deploys foundation infrastructure resources in Azure that can be used by organisations to prepare their subscription for migration of virtual machines. It also helps establish governance controls necessary to manage their cloud estate. The sample will deploy and enforce resources, policies, and templates that will allow an organisation to get started with Azure.
The key difference between Azure and AWS is that while AWS landing zone solution takes a holistic view of the organisation when automatically setting up it’s accounts, policies etc, the Azure blueprint tackles the problem at the subscription level. The creation of the management group, subscription design etc is completed manually beforehand.
The blueprint is closer to the AWS Landing Zone solution than AWS Control Tower in that there is no UI and is run as infrastructure as code with parameters. The Azure documentation is comprehensive and well laid out to follow.
Other Blueprints
Azure also provides a blueprint library that contains a list of all the main controls required by different organisations around the world and guidelines on how to implement. Some key ones are:
CIS Microsoft Azure Foundations Benchmark blueprint - provides governance guard-rails using Azure Policy that help you assess specific CIS Microsoft Azure Foundations Benchmark recommendations.
Control mapping of the Australian Government ISM PROTECTED blueprint - provides a long set of guidelines required for the Australian government in regards to the controls required.
Landing Zone expansion
One aspect Azure makes clear is that the initial landing zone is just that - an initial landing zone. They emphasise the need to constantly “refactor” the design and update the implementation as new requirements arise.
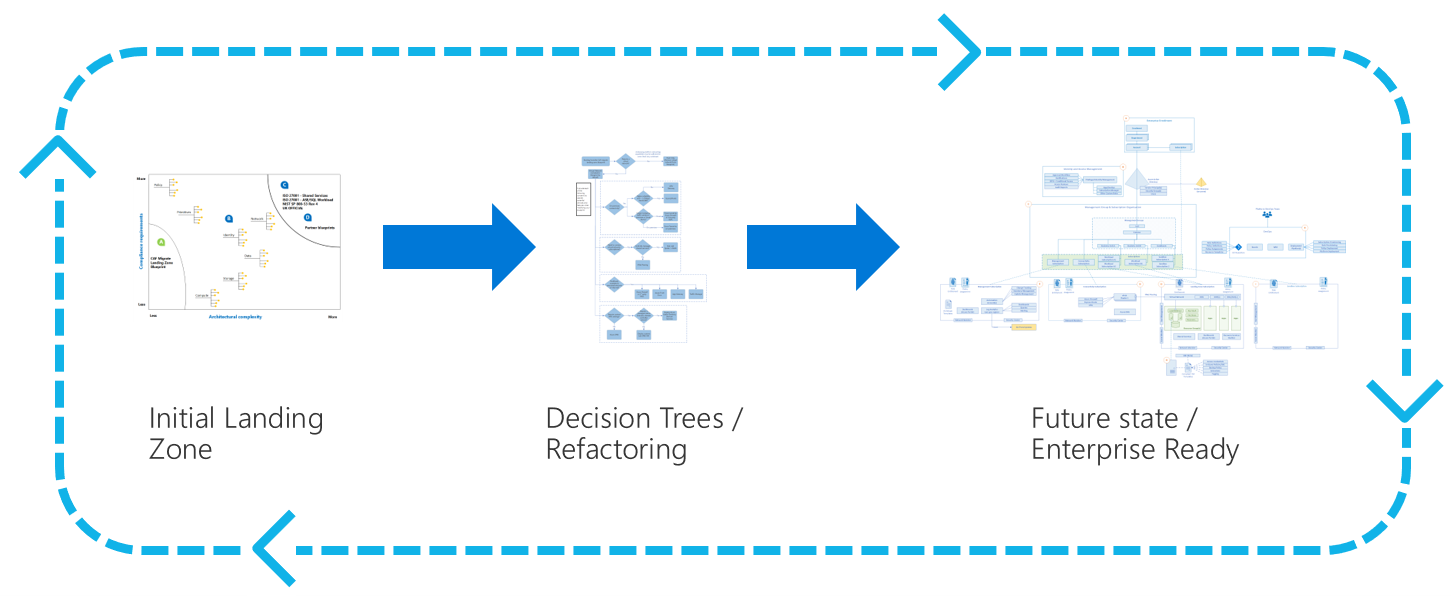
refactor.png
References
CAF Migration landing zone blueprint sample overview - Azure Blueprints | Microsoft Docs
GCP
As a bit of a primer, GCP’s main way of organising resources is the concept of creating projects that allow you to structure resources hierarchically in the same account. These projects can then be organised in a simple hierarchy underneath your organisation account.
By default, resources within a Project are accessible to other resources in that Project (as long as their API is enabled) and are inaccessible to anything outside of the project. This goes a long way towards setting up safe permission structures. If you need to, you can easily setup inter-project resource access.
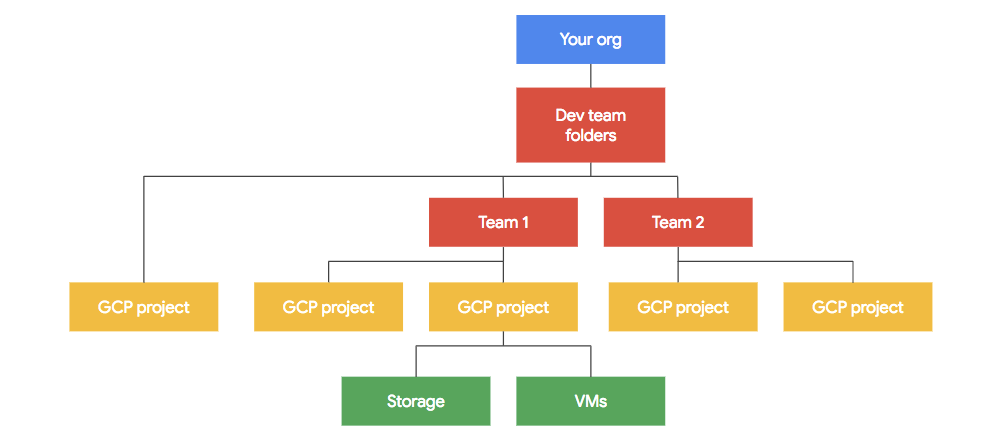
GCP doesn’t necessarily talk about building a landing zone but it does have a pretty detailed list of the items you need to consider when setting up your organisation's environments. GCP’s documentation pages are typically lean, to the point, crisp and clear. Their best practices for enterprise organisations document is no different.
So if the main question is “what kind of support do I have to create a secure and best practice implementation” then GCP still provides some solid advice through its guidelines even if it doesn’t provide automated solutions. Since Google started a bit later, and while it doesn’t yet have the breadth of services AWS has, it had the benefit of starting with a clean slate and therefore you could say things are a little bit cleaner and well thought through. So maybe it doesn’t need the landing zone solution as much.
Having said that, there does look like there are some open source projects that are building out some approaches to a automated CGP landing zone.
References
https://cloud.google.com/docs/enterprise/best-practices-for-enterprise-organizations
Summary
There are various levels of documentation and automation provided by the main cloud providers to assist you in setting up your landing zone.
As your use of the cloud expands, you will be required to build on and evolve the landing zone as requirements change and new features are released. Ensure that the structures you put in place are not too ridged. Otherwise, you may find that growth and evolution become more difficult to achieve.
Ultimately a landing zone should not simply be the start of your journey into the cloud, but a constantly evolving core component of your infrastructure that should be well thought out and strategised.
Your AWS, Azure and GCP monthly news roundup
Join our list to receive The Radar delivered directly to your inbox on a monthly basis.








